Zomato has sought to assure users that their passwords is safe after being stolen from their database yesterday, but new reports are now questioning their claims.
Zomato’s a fairly well-known brand across the world, so its hack has attracted the attention of the world media. Among the publications that were tracking the developments was Vice. Vice reporters downloaded the sample that was available on the Dark Web, and with relatively little effort, were able to crack “over half” of the passwords.

“(We) pasted the sample into an online hash checker, which compares the data to a list of already cracked hashes. The service successfully returned just over half of the users’ alleged passwords,” said Vice. The easiest passwords to guess were those which were commonly used, such as “password” or “qwerty”.
Zomato’s passwords were hashed with a “one-way hashing algorithm with multiple iterations”. This means that users’s passwords weren’t stored in plain text in Zomato’s servers, but after passing the passwords through a function. This function converts simple passwords into a complex string of characters. The function, which in Zomato’s case was MD5, produces same results each time it’s applied on the same string — this means that someone with access to the “complex strings” can run the same function against a list of common passwords, and if the resulting “complex strings” match, can determine the original password.
To prevent against this, companies attach a “salt” to passwords, which are a random strings appended to the password. This adds an additional layer of complexity, making it harder for people with access to the “complex strings” to guess the original passwords. But the sample uploaded by the hacker showed that Zomato had used a salt that was only two characters long.
“Whilst a salt was appended to the hashes, it was only 2 characters long and provided virtually no benefit. Along with this, the MD5 hashing algorithm is outdated and has been superseded by more cryptographically secure hashing algorithms,” a security researcher told Vice.
Zomato’s passwords were available for sale on the Dark Web for several hours before they were taken down, so it’s very possible that an unscrupulous party could’ve purchased the entire list. Using a simple approach, it could be possible to crack passwords for an extremely large number of email accounts. Users who use the same password across multiple sites are particularly vulnerable — if hacker discovers your Zomato password, and you’ve used the same password at another site, they could theoretically gain access to your credentials on that site as well.
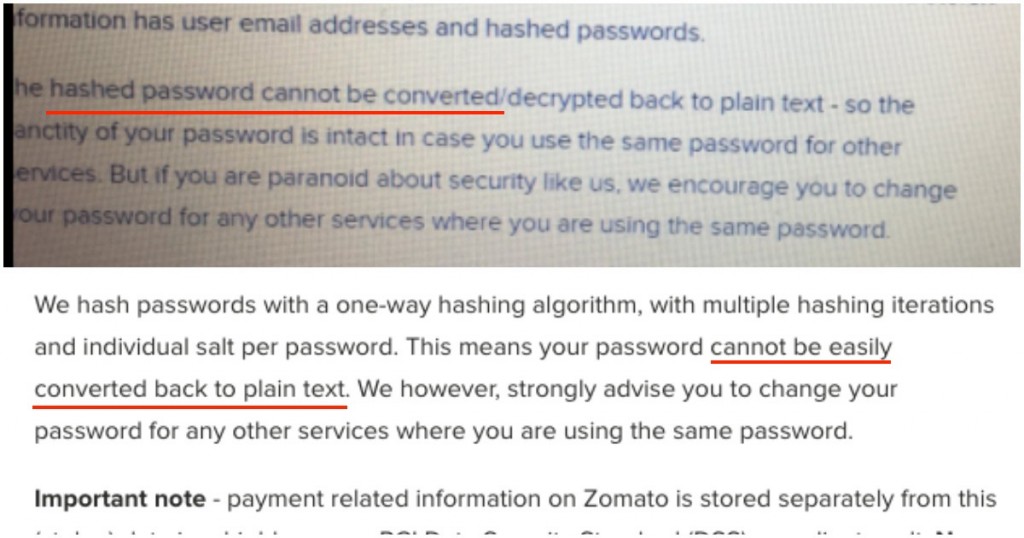
Zomato, too, has been cagey about its vulnerability. In its original blogpost, it had claimed that “the hashed password cannot be converted into plain text”. Hours later, it had updated its post to read that the “password cannot be easily converted back to plain text,” after several researchers had pointed out that it was indeed possible to convert a hashed password to plain text.
Given how Vice now claims that over half of the passwords can be cracked, it’s clear that Zomato’s user passwords are extremely vulnerable. While the company has already reset affected passwords on its own site, and also said that they”strongly advise you to change your password for any other services where you are using the same password,” it probably bears repeating: if you were using the same password as Zomato on other service, it’s imperative that you change it immediately.
